Identity and Access Management: Strengthening Digital Trust
As organizations expand across cloud platforms, remote work environments, and third-party integrations, identity has become the new security perimeter. Identity and Access Management (IAM) plays a critical role in ensuring that the right individuals have the appropriate level of access to systems, data, and applications.
Without strong IAM controls, even advanced security technologies can fail. Compromised credentials remain one of the leading causes of security breaches, making identity protection a foundational element of modern cybersecurity strategy.

What Is Identity and Access Management?
IAM is a framework of policies, technologies, and processes that manage digital identities and control access to organizational resources. It ensures that users are authenticated, authorized, and audited throughout their interactions with systems.
Effective IAM balances security with usability, enabling secure access while minimizing friction for employees, partners, and customers.
- User identity lifecycle management.
- Authentication and authorization controls.
- Access governance and auditing.
- Policy enforcement across environments.
Why IAM Is Critical in Modern Enterprises
Digital transformation has dissolved traditional network boundaries. Users now access applications from multiple locations, devices, and networks, increasing exposure to credential-based attacks.
IAM provides centralized visibility and control, reducing the risk of unauthorized access and limiting the impact of compromised credentials.
- Reduces insider and external access risks.
- Supports secure remote and hybrid work.
- Improves compliance with regulatory requirements.
- Enhances visibility into access behavior.
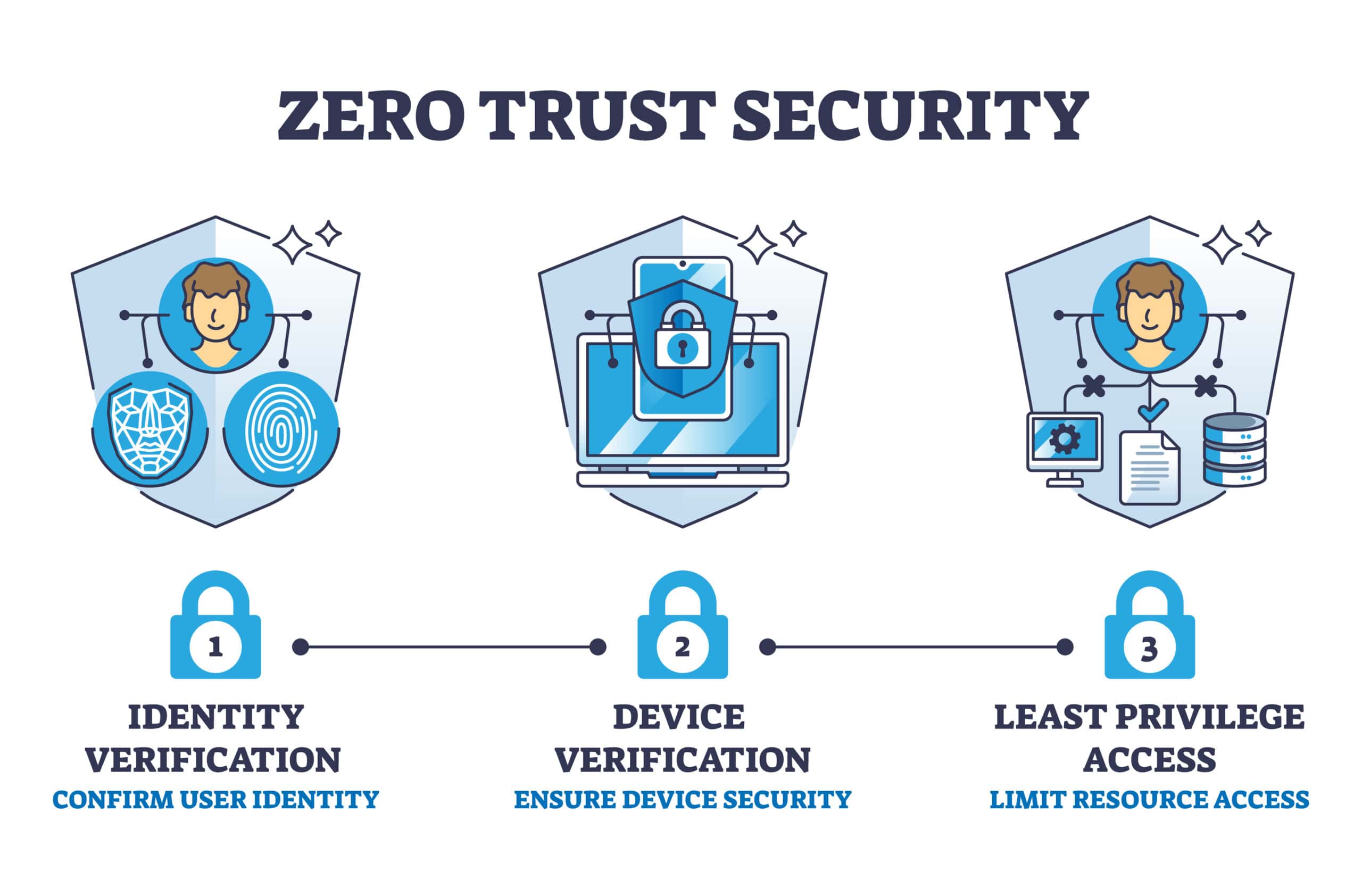
Core IAM Components
A comprehensive IAM strategy includes multiple components working together to enforce access control and maintain accountability.
- Multi-Factor Authentication (MFA) for stronger verification.
- Role-Based and Attribute-Based Access Control.
- Single Sign-On (SSO) for centralized authentication.
- Privileged Access Management (PAM) for high-risk accounts.
Common IAM Challenges
Despite its importance, IAM implementations can be complex. Poorly designed access policies or outdated processes can create security gaps and operational inefficiencies.
Organizations must regularly review identities, access rights, and system integrations to ensure IAM controls remain effective.
- Overprivileged accounts and access sprawl.
- Legacy systems lacking modern identity controls.
- Manual user provisioning and deprovisioning.
- Limited visibility into third-party access.
Building a Strong IAM Strategy
An effective IAM program aligns technology, policy, and governance. Organizations should adopt a risk-based approach that prioritizes critical assets and sensitive identities.
- Apply least privilege access by default.
- Enforce MFA across users and administrators.
- Continuously monitor and review access activity.
- Integrate IAM into Zero Trust architectures.
Conclusion
Identity and Access Management is no longer optional-it is a core requirement for protecting modern digital environments. By strengthening identity controls, organizations can reduce breach risk, improve compliance, and support secure business growth.
A mature IAM strategy, combined with continuous monitoring and governance, enables enterprises to build lasting digital trust in an increasingly complex threat landscape.



Leave a Reply