ISO 27001 Implementation Guide for Businesses
Information security has become a critical business requirement as organizations face increasing cyber threats, regulatory scrutiny, and customer expectations. ISO/IEC 27001 is the internationally recognized standard for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS).
For businesses, ISO 27001 certification demonstrates a structured and risk-based approach to protecting sensitive information. This guide explains the key steps, best practices, and strategic considerations involved in implementing ISO 27001 successfully.
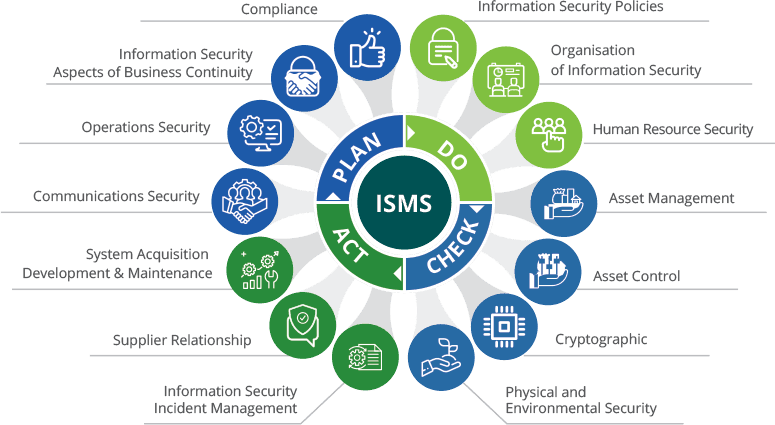
Understanding ISO 27001 and ISMS
ISO 27001 provides a systematic approach to managing information security risks. At its core is the Information Security Management System (ISMS), a framework that helps organizations identify, assess, and mitigate risks to information assets.
The standard is applicable to organizations of all sizes and industries, covering people, processes, and technology.
- Defines security controls aligned with risk assessment.
- Applies to digital, physical, and intellectual information assets.
- Supports regulatory and contractual compliance.
- Promotes continual improvement of security posture.
Defining Scope and Leadership Commitment
Successful ISO 27001 implementation begins with clearly defining the scope of the ISMS. Organizations must identify which business units, systems, processes, and data are included.
Equally important is leadership commitment. Top management must support the initiative, allocate resources, and establish information security as a strategic priority.
- Define ISMS boundaries and objectives.
- Identify internal and external stakeholders.
- Assign roles and responsibilities.
- Demonstrate leadership involvement and accountability.

Risk Assessment and Risk Treatment
Risk assessment is the foundation of ISO 27001. Organizations must identify information security risks, evaluate their likelihood and impact, and determine appropriate treatment options.
The risk treatment process aligns selected controls with business risk appetite and operational requirements.
- Identify threats, vulnerabilities, and assets.
- Assess risks based on likelihood and impact.
- Select appropriate Annex A controls.
- Document risk treatment plans and decisions.
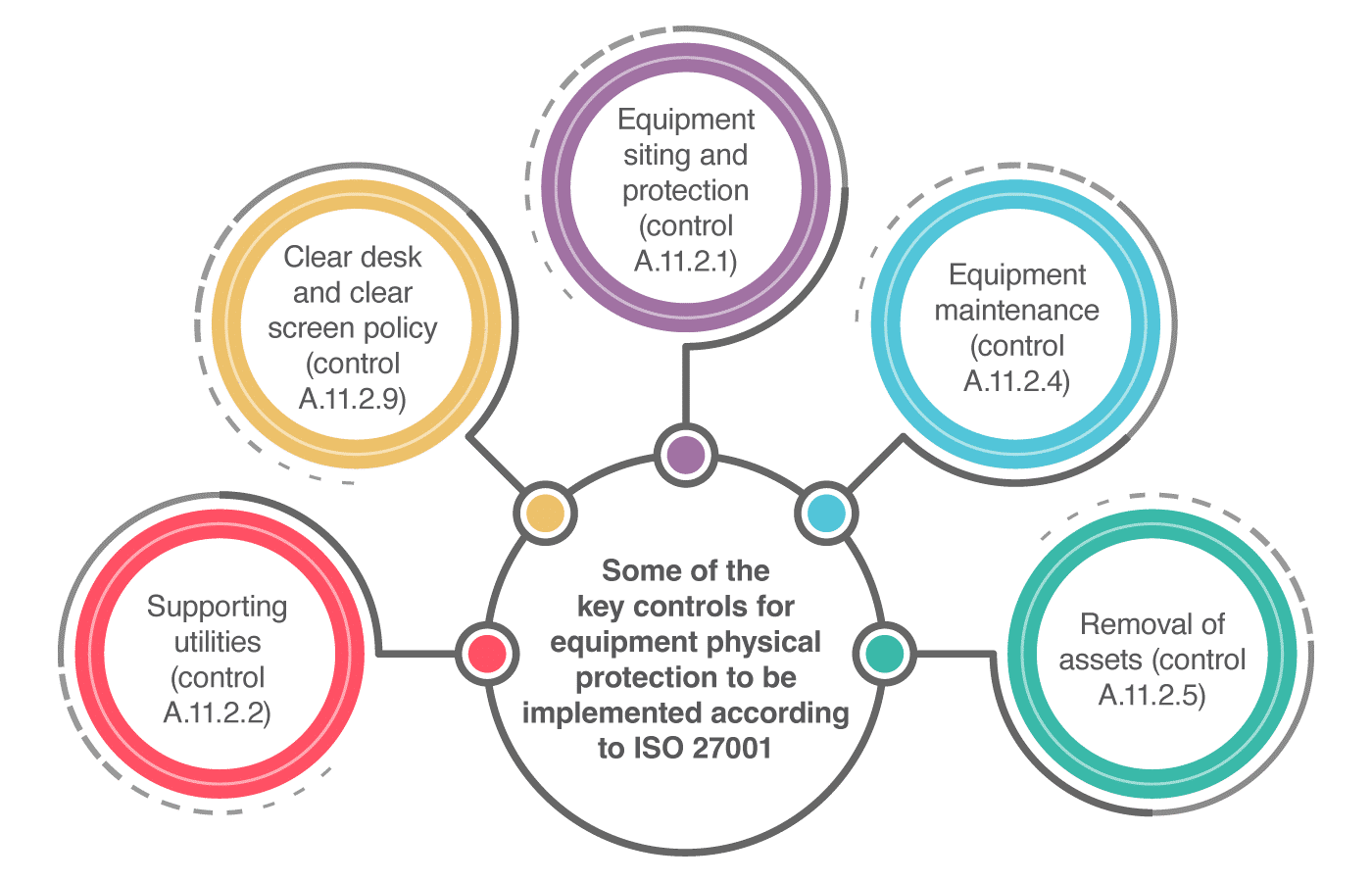
Implementing Security Controls
ISO 27001 Annex A outlines a comprehensive set of security controls covering areas such as access control, cryptography, operations security, supplier relationships, and incident management.
Controls must be implemented based on risk assessment outcomes and integrated into daily business operations.
- Access control and identity management.
- Data protection and encryption.
- Incident detection and response procedures.
- Supplier and third-party risk management.
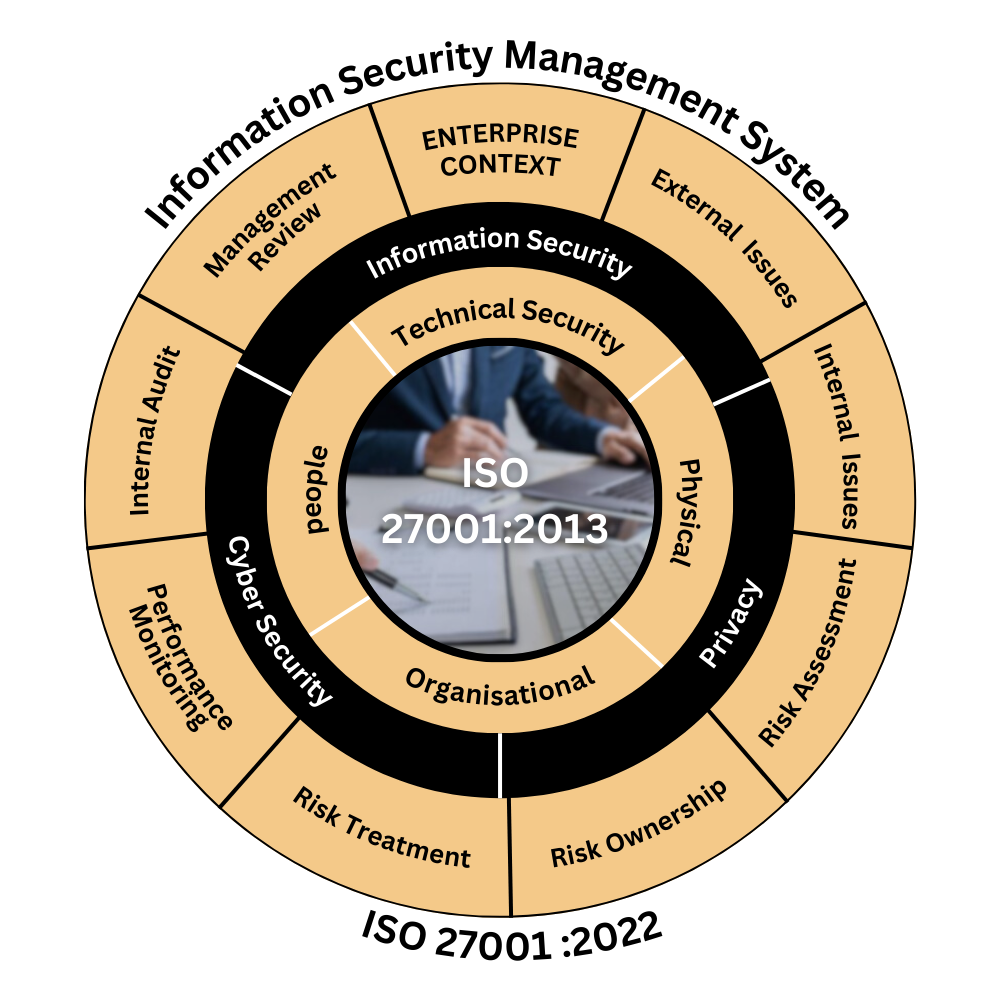
Monitoring, Audits, and Continuous Improvement
ISO 27001 is not a one-time project. Organizations must continuously monitor performance, conduct internal audits, and review ISMS effectiveness.
Regular audits and management reviews help identify gaps, ensure compliance, and drive continuous improvement.
- Monitor KPIs and security metrics.
- Conduct periodic internal audits.
- Perform management reviews.
- Address nonconformities and improve controls.
Conclusion
Implementing ISO 27001 provides businesses with a structured, internationally recognized approach to managing information security risks. It strengthens governance, improves operational resilience, and enhances stakeholder confidence.
By following a risk-based methodology, engaging leadership, and committing to continuous improvement, organizations can achieve sustainable information security and long-term compliance success.


Leave a Reply