-
Identity and Access Management: Strengthening Digital Trust

Identity and Access Management: Strengthening Digital Trust Identity and Access Management: Strengthening Digital Trust As organizations expand across cloud platforms, remote work environments, and third-party integrations, identity has become the new security perimeter. Identity and Access Management (IAM) plays a critical role in ensuring that…
-
Top Threat Intelligence Practices for 2026

Top Threat Intelligence Practices for 2026 Top Threat Intelligence Practices for 2026 As cyber threats grow in sophistication, threat intelligence has become a foundational pillar of modern cybersecurity strategy. In 2026, organizations face AI-powered attacks, highly targeted intrusions, ransomware-as-a-service, and supply chain compromises that demand…
-
Email Phishing Trends and How to Protect Your Team

Email Phishing Trends and How to Protect Your Team Email Phishing Trends and How to Protect Your Team Email phishing continues to be one of the most effective and widespread cyberattack techniques. Despite advances in security technology, attackers exploit human trust, urgency, and familiarity with…
-
ISO 27001 Implementation Guide for Businesses
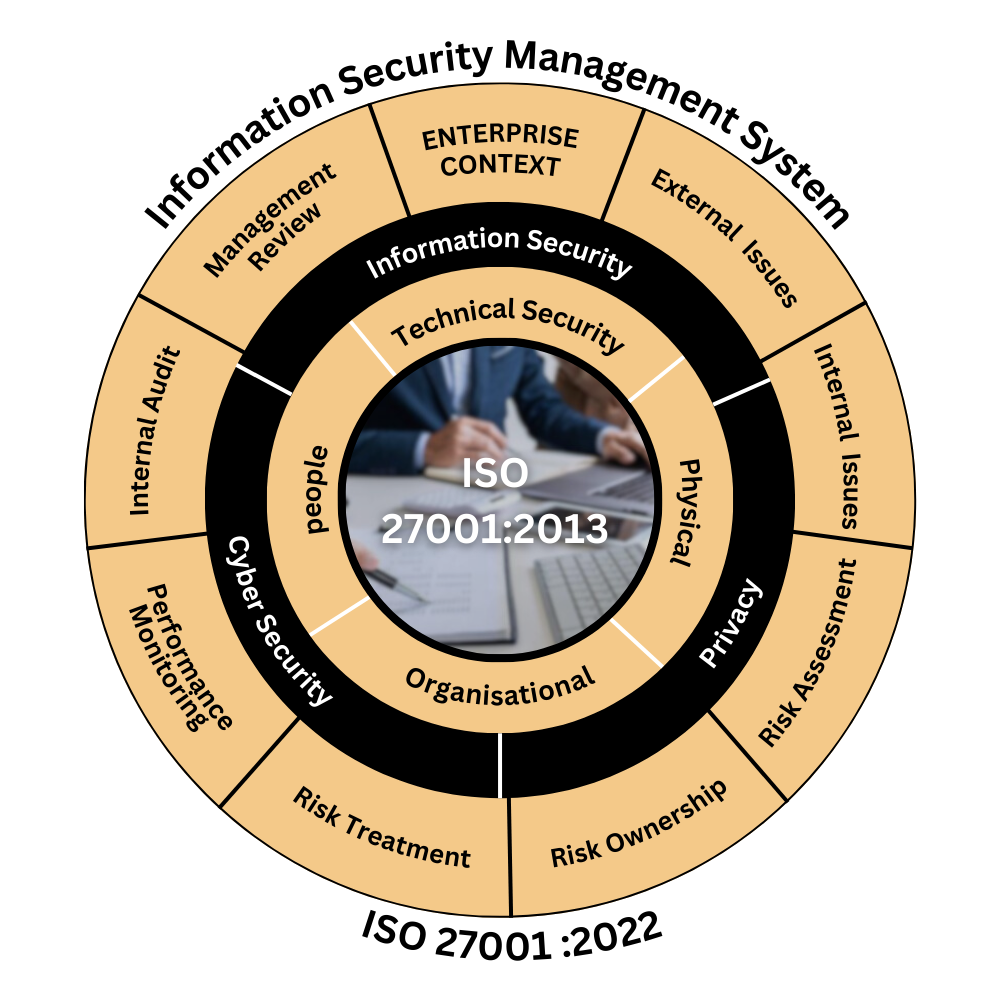
ISO 27001 Implementation Guide for Businesses ISO 27001 Implementation Guide for Businesses Information security has become a critical business requirement as organizations face increasing cyber threats, regulatory scrutiny, and customer expectations. ISO/IEC 27001 is the internationally recognized standard for establishing, implementing, maintaining, and continually improving…
-
Building a Cybersecurity Awareness Program for Employees

Building a Cybersecurity Awareness Program for Employees Building a Cybersecurity Awareness Program for Employees Human error remains one of the leading causes of cybersecurity incidents across organizations of all sizes. Despite investments in advanced security technologies, a single uninformed employee can inadvertently expose systems to…
-
AI and Cybersecurity: Opportunities and Threats

AI and Cybersecurity: Opportunities and Threats AI and Cybersecurity: Opportunities and Threats Artificial Intelligence (AI) is reshaping the cybersecurity landscape at an unprecedented pace. Organizations increasingly rely on AI-driven systems to detect threats, automate responses, and analyze vast amounts of security data. At the same…

