Third-Party Risk Management: Securing Your Extended Enterprise
Modern organizations depend heavily on third parties such as cloud providers, vendors, contractors, and managed service providers. While these relationships enable efficiency and innovation, they also expand the organization’s attack surface.
Third-party risk management (TPRM) focuses on identifying, assessing, and controlling risks introduced by external entities. Without a structured approach, organizations may inherit security weaknesses beyond their direct control.
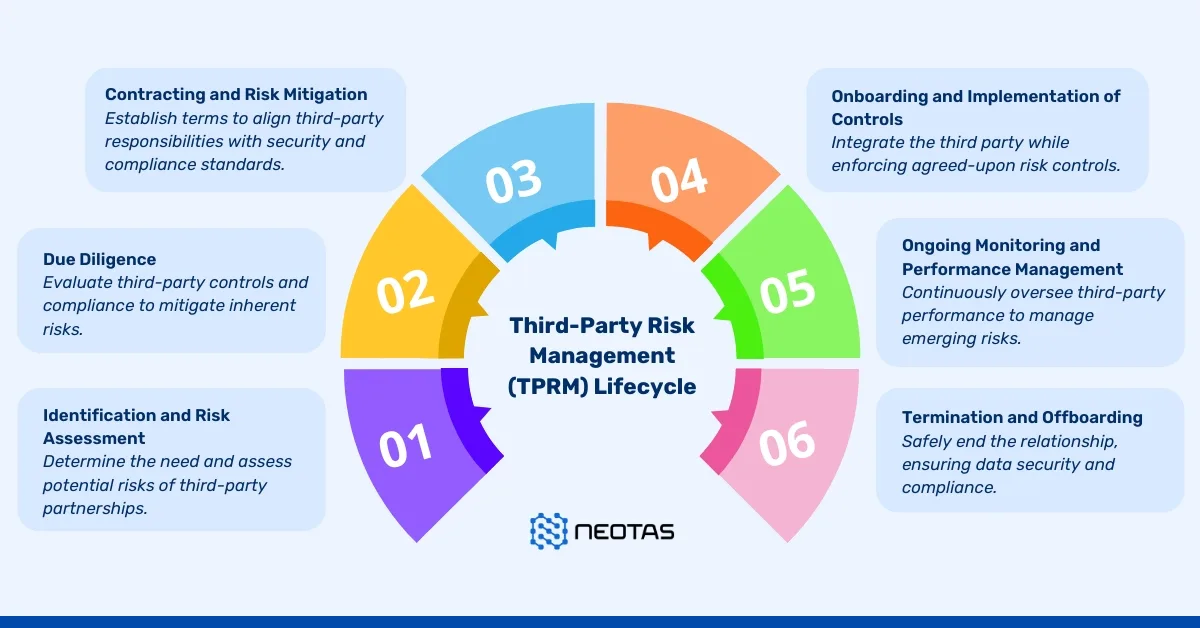
Why Third-Party Risk Matters
Many high-impact security incidents originate from compromised vendors rather than internal systems. Attackers target third parties because they often have privileged access and fewer security controls.
As ecosystems grow more interconnected, organizations must treat vendor risk as an extension of internal risk management.
- Vendors often access sensitive data or systems.
- Security maturity varies across third parties.
- Supply chain attacks can bypass perimeter defenses.
- Regulatory accountability remains with the organization.
Common Third-Party Security Risks
Third-party risks are not limited to data breaches. Operational disruptions, compliance failures, and reputational damage can result from vendor security incidents.
Understanding common risk categories helps organizations prioritize controls and oversight.
- Inadequate access controls and credential management.
- Weak patching and vulnerability management.
- Data handling and privacy violations.
- Dependency on single critical vendors.

Assessing Third-Party Security Posture
Effective TPRM begins with visibility. Organizations must understand who their vendors are, what access they have, and what data they handle.
Risk assessments should be proportionate to vendor criticality and business impact.
- Maintain an up-to-date vendor inventory.
- Classify vendors by risk and access level.
- Use questionnaires, audits, or attestations.
- Review compliance with relevant standards.
Managing Risk Through Governance and Controls
Assessment alone is insufficient without governance. Organizations must define expectations and enforce security requirements throughout the vendor lifecycle.
Contracts, policies, and monitoring mechanisms help ensure accountability.
- Include security clauses in vendor contracts.
- Define incident reporting and response obligations.
- Monitor vendor performance continuously.
- Reassess risk during renewals or changes.
Building a Sustainable Third-Party Risk Program
A mature TPRM program integrates security, procurement, legal, and business teams. Collaboration ensures that security requirements align with operational needs.
Sustainable programs evolve with changing threats and business relationships.
- Embed risk management into procurement processes.
- Automate assessments where appropriate.
- Educate internal teams on vendor risk.
- Continuously improve based on incidents.
Conclusion
Third-party risk management is no longer optional in today’s interconnected digital environment. Organizations must recognize that vendor relationships extend their security boundaries.
By applying structured assessment, governance, and continuous oversight, enterprises can reduce supply chain exposure while maintaining trusted partnerships.


Leave a Reply