Top Threat Intelligence Practices for 2026
As cyber threats grow in sophistication, threat intelligence has become a foundational pillar of modern cybersecurity strategy. In 2026, organizations face AI-powered attacks, highly targeted intrusions, ransomware-as-a-service, and supply chain compromises that demand proactive, intelligence-driven defenses.
Threat intelligence is no longer limited to collecting indicators of compromise. It now requires contextual analysis, enterprise-wide collaboration, and predictive capabilities that allow organizations to stay ahead of adversaries rather than react after damage occurs.

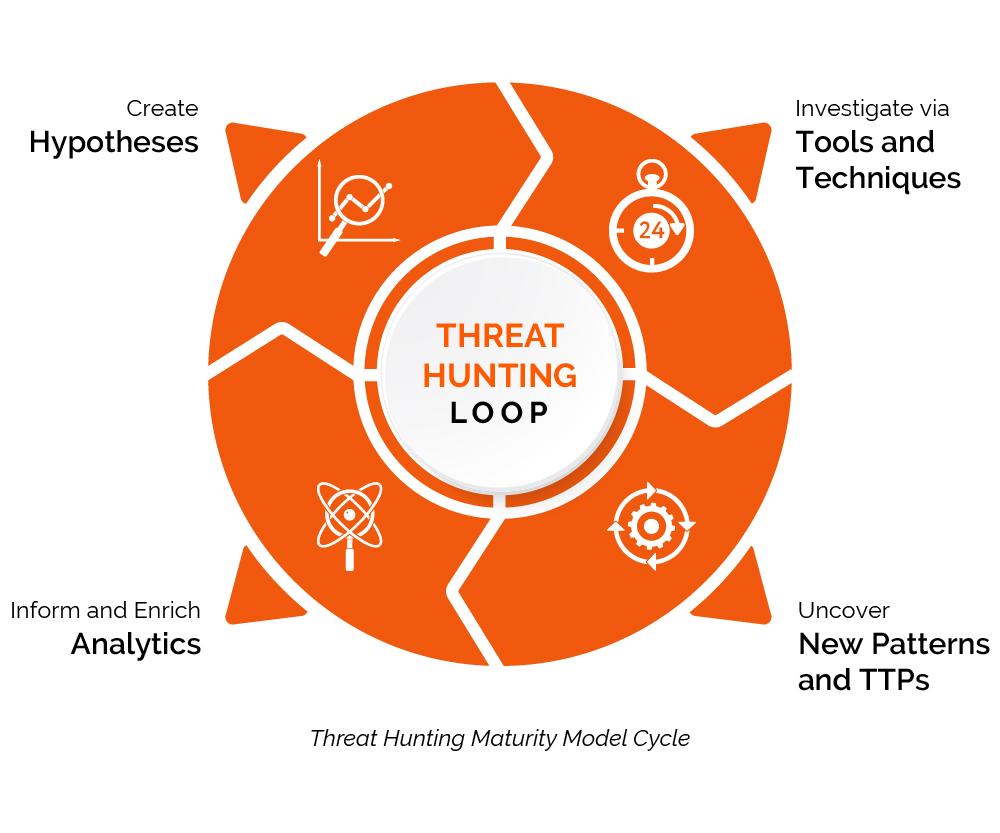
Proactive Threat Hunting
Proactive threat hunting focuses on identifying hidden threats before automated tools generate alerts. Rather than waiting for security systems to trigger alarms, analysts actively search for suspicious behaviors, anomalies, and attacker techniques within the environment.
This approach significantly reduces dwell time and improves detection of advanced persistent threats that bypass traditional defenses.
- Analyze abnormal user, network, and endpoint behavior.
- Correlate telemetry across cloud, endpoint, and identity platforms.
- Develop hypothesis-driven investigations.
- Create repeatable playbooks for common threat scenarios.
Threat Intelligence Platform (TIP) Integration
Threat Intelligence Platforms consolidate internal and external threat data into a centralized system, enabling faster analysis and decision-making. In 2026, TIPs play a critical role in operationalizing intelligence across security operations.
By integrating TIPs with SIEM, SOAR, EDR, and network controls, organizations can automate response workflows and prioritize high-risk threats based on business impact.
- Aggregate multiple threat feeds and intelligence sources.
- Automate enrichment and correlation of indicators.
- Reduce alert fatigue through contextual prioritization.
- Enable collaboration across SOC, IT, and risk teams.
Enterprise-Wide Intelligence Sharing
Threat intelligence is most effective when shared beyond the security team. Executive leadership, compliance teams, IT operations, and business units all benefit from understanding emerging threats and risk exposure.
Clear communication ensures faster response, improved governance, and alignment between security initiatives and business objectives.
- Provide executive-level threat summaries and dashboards.
- Share intelligence across SOC, IT, and risk management teams.
- Establish standardized response procedures.
- Translate technical risks into business impact.
AI and Machine Learning in Threat Intelligence
Artificial intelligence and machine learning are transforming how threat intelligence is generated and consumed. These technologies analyze massive data volumes to identify patterns, predict attacks, and detect anomalies faster than human analysts.
AI-driven intelligence enables security teams to focus on high-impact threats while reducing manual analysis and response time.
- Detect unknown threats through behavioral analysis.
- Predict attacker tactics using historical data.
- Automate triage and prioritization.
- Continuously adapt models to evolving threats.
Continuous Threat Landscape Monitoring
The threat landscape evolves constantly, making continuous monitoring essential. Organizations must track emerging vulnerabilities, malware variants, geopolitical risks, and adversary techniques.
Regular assessments ensure that security controls remain effective and aligned with real-world threats.
- Monitor industry threat reports and advisories.
- Participate in intelligence-sharing communities.
- Conduct red team and blue team exercises.
- Update policies based on emerging risks.
Conclusion
In 2026, threat intelligence is a strategic necessity rather than a technical add-on. Organizations that invest in proactive hunting, AI-driven analysis, intelligence sharing, and continuous monitoring are better positioned to defend against advanced cyber threats.
By embedding threat intelligence into security operations and business decision-making, enterprises can reduce risk, improve resilience, and stay ahead of an increasingly sophisticated adversary landscape.



Leave a Reply