Zero Trust Security: Moving Beyond Perimeter-Based Defense
Traditional cybersecurity models were built on the assumption that systems inside the network could be trusted. However, modern enterprises operate across cloud platforms, remote workforces, and third-party integrations, rendering perimeter-based security increasingly ineffective.
Zero Trust Security challenges this outdated assumption by enforcing continuous verification and strict access control. Instead of trusting users or devices by default, Zero Trust requires validation at every stage of access.

Understanding the Zero Trust Model
Zero Trust is a security philosophy rather than a single product or technology. It is based on the principle of “never trust, always verify,” ensuring that every access request is evaluated regardless of location.
This model treats internal and external networks with equal caution, reducing the impact of compromised credentials or insider threats.
- No implicit trust based on network location.
- Continuous authentication and authorization.
- Strict enforcement of least privilege access.
- Ongoing monitoring of user and device behavior.
Why Perimeter-Based Security Falls Short
Perimeter defenses such as firewalls and VPNs were designed for centralized environments. As systems move to the cloud and users connect remotely, attackers can bypass or exploit these defenses.
Once inside the network, traditional models often allow lateral movement, increasing the potential damage of a single breach.
- Increased exposure due to remote and hybrid work.
- Limited visibility into internal traffic.
- Credential-based attacks bypass perimeter controls.
- Overreliance on network location as a trust factor.
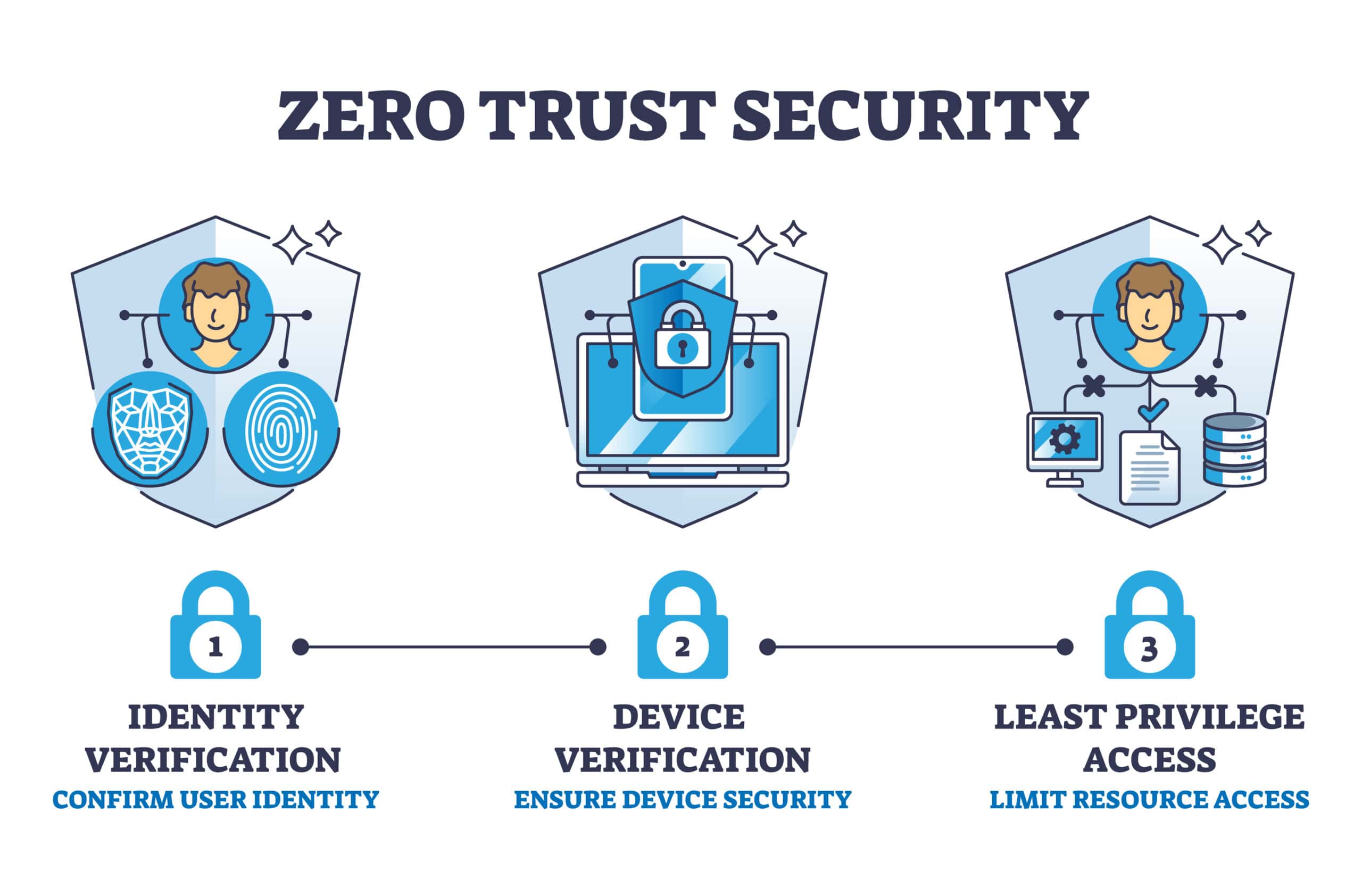
Core Principles of Zero Trust
Zero Trust frameworks are built on several foundational principles that guide secure access and resource protection across environments.
- Verify explicitly using multiple identity and context signals.
- Apply least privilege access to limit exposure.
- Assume breach and design controls accordingly.
- Continuously monitor and assess risk.
Implementing Zero Trust in Practice
Adopting Zero Trust is a gradual process that requires alignment across identity, devices, applications, and data. Organizations should prioritize high-risk access points and critical assets first.
Successful implementations focus on visibility, governance, and user experience to ensure security does not hinder productivity.
- Strengthen identity verification with MFA.
- Segment networks and applications.
- Monitor access continuously for anomalies.
- Integrate Zero Trust with existing security controls.
Zero Trust as a Long-Term Strategy
Zero Trust is not a one-time deployment but an evolving strategy. As threats change and environments grow, policies and controls must adapt accordingly.
Organizations that embed Zero Trust into their security culture are better equipped to manage risk, support digital transformation, and maintain resilience.
- Regularly review access policies.
- Align Zero Trust with business objectives.
- Educate teams on shared responsibility.
- Measure effectiveness through continuous improvement.
Conclusion
Zero Trust Security represents a fundamental shift in how organizations protect digital assets. By eliminating implicit trust and enforcing continuous verification, enterprises can reduce breach impact and improve overall security posture.
As digital ecosystems continue to evolve, Zero Trust provides a scalable and resilient foundation for modern cybersecurity strategies.


Leave a Reply