-
Security Governance: Aligning Cybersecurity with Business Strategy
Security Governance: Aligning Cybersecurity with Business Strategy Security Governance: Aligning Cybersecurity with Business Strategy Cybersecurity failures are rarely caused by missing tools or weak technology alone. In many cases, breaches occur because security decisions are disconnected from business strategy, leadership priorities, and organizational accountability. Security…
-
Third-Party Risk Management: Securing Your Extended Enterprise
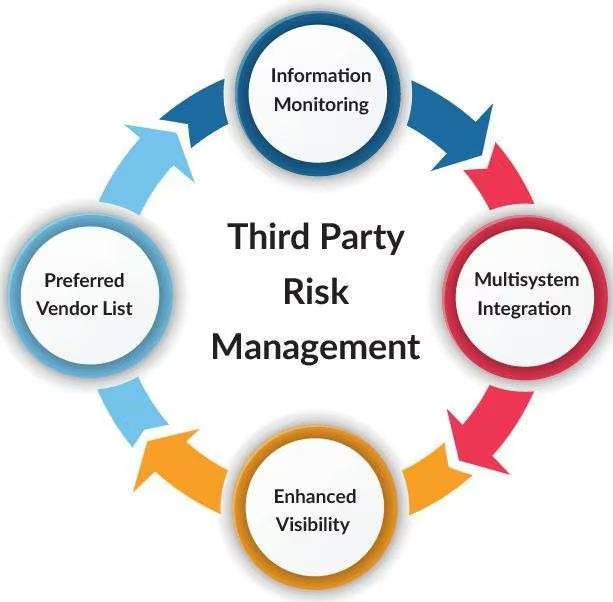
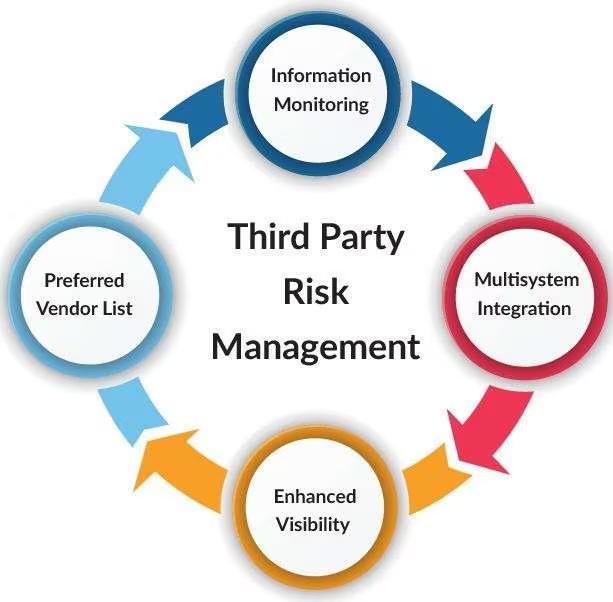
Third-Party Risk Management: Securing Your Extended Enterprise Third-Party Risk Management: Securing Your Extended Enterprise Modern organizations depend heavily on third parties such as cloud providers, vendors, contractors, and managed service providers. While these relationships enable efficiency and innovation, they also expand the organization’s attack surface.…
-
Incident Response and Breach Readiness: Preparing for the Inevitable
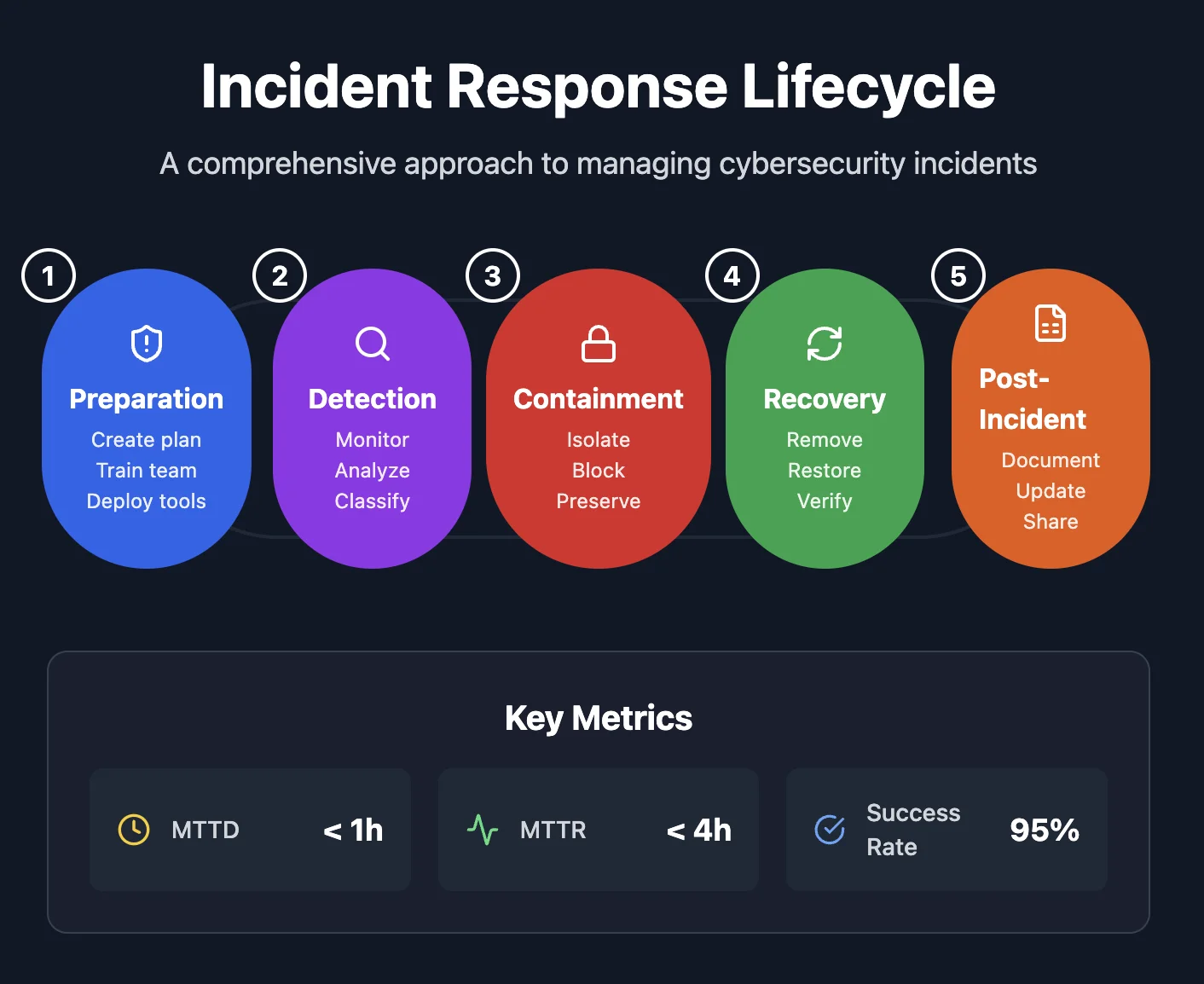
Incident Response and Breach Readiness: Preparing for the Inevitable Incident Response and Breach Readiness: Preparing for the Inevitable Cyber incidents are no longer a matter of “if” but “when.” Even organizations with strong preventive controls can experience breaches due to sophisticated attacks, human error, or…
-
Data Loss Prevention (DLP): Protecting Sensitive Information in the Modern Enterprise
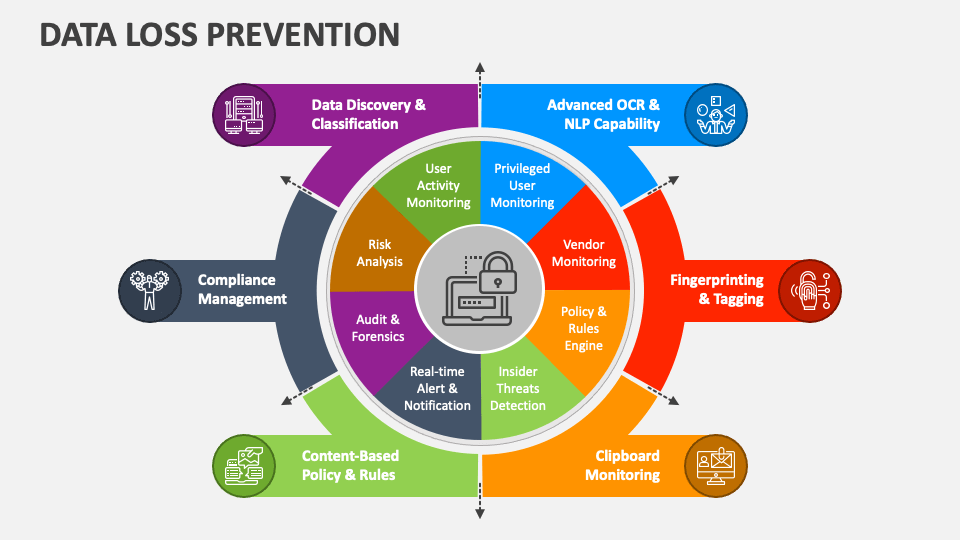
Data Loss Prevention (DLP): Protecting Sensitive Information in the Modern Enterprise Data Loss Prevention (DLP): Protecting Sensitive Information in the Modern Enterprise Data is one of the most valuable assets an organization owns. Customer records, intellectual property, financial information, and proprietary research all represent critical…
-
Cloud Security and the Shared Responsibility Model Explained

Cloud Security and the Shared Responsibility Model Explained Cloud Security and the Shared Responsibility Model Explained Cloud computing has transformed how organizations deploy, scale, and manage technology. While cloud platforms offer flexibility and efficiency, they also introduce new security responsibilities that are often misunderstood. The…
-
Zero Trust Security: Moving Beyond Perimeter-Based Defense
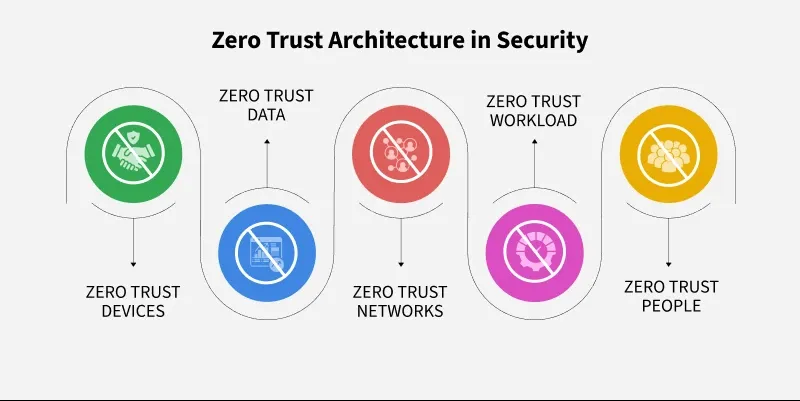
Zero Trust Security: Moving Beyond Perimeter-Based Defense Zero Trust Security: Moving Beyond Perimeter-Based Defense Traditional cybersecurity models were built on the assumption that systems inside the network could be trusted. However, modern enterprises operate across cloud platforms, remote workforces, and third-party integrations, rendering perimeter-based security…

